Introduction
In an industry replete with products that promise risk mitigation, RFID solutions stand out as a surefire way to cost-effectively and reliably minimize risk by enforcing accountability throughout the enterprise, no matter how expansive or complex.
RFID has long been used for toll collection, animal tracking, automobile immobilization, pharmaceuticals, assembly line tracking, etc. — any application where an RFID tag can be applied to track progress and location.

High efficiency, low cost and consistent reliability of RFID systems and tags are driving demand in applications that require real time information on asset allocation, alerts when protected assets breach secured zones and comprehensive reports on usage. This high growth is due in part to rising awareness of the advantages associated with RFID systems and their ability to integrate with existing business applications.
This white paper discusses three ways to bring your customers immediate and significant benefits from Accountability through RFID.
Essential Information on Asset Allocation and Usage
RFID is used to keep track of virtually anything: laptops, lab equipment, vehicles, drugs, weapons. Usage of these assets can be monitored to ensure regular maintenance for safety and insurance purposes. For example, customers managing a fleet of trucks, cars or other vehicles can use RFID to help control the vehicle inventory, maintenance, vehicle mileage status, accident history, driver assignments and more — all from one management software.

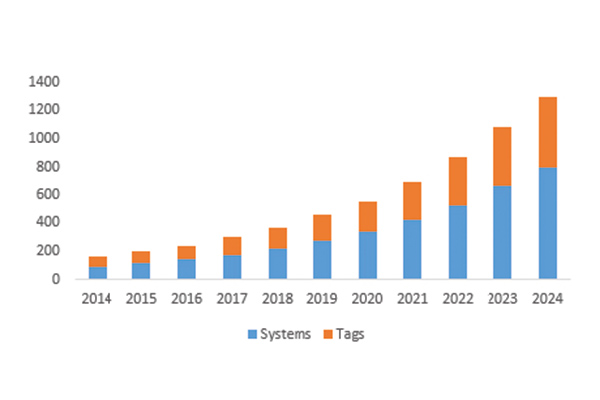
In healthcare applications, RFID is expected to see double-digit growth (refer to figure 1), because of increasing demand for location identification of critical healthcare equipment. Hospitals are looking to RFID solutions to provide real time information on availability and condition of life-saving equipment. By explicitly assigning and automatically monitoring access to critical equipment as well as its usage, RFID solutions can ensure availability and optimal working condition – something that simply cannot be compromised in a healthcare setting.
Benefits
- Improves maintenance
- Lowers equipment costs
- Lower insurance premiums
Protect Integrity of Evidence through Electronic Chain-of-Custody
Patents, customer data, intellectual property, proprietary information–these are some of the most important ways a company can monetize its value and differentiate itself in its competitive market. Controlling who has access to this information requires more than a simple check-in, check-out process, and RFID can provide all the software and hardware needed to keep an electronic chain-of-custody.
• Law enforcement agencies rely on RFID to track new issuance of weapons and transfer of evidence by capturing digital signatures at the
time of the transactions.
• Software development and technology companies use RFID solutions to enforce strict rules of hard drive or prototype exchanges
between R&D groups.

RFID solutions strictly enforce chain-of-custody for evidence, intellectual property, high-value data, research materials, and dangerous items such as firearms. Employing verified groups or powerful two-man or three-man rules permit sensitive or restricted keys to be released only when the required logins are approved.
In many cases, one group of RFID tag holders is permitted to open a secured locker or smart storage container to place an asset, while another group is only allowed to retrieve items. Chain of Custody and audit trail reports provide maximum accountability of property exchange.
Benefits
- Protects company value and reputation
- Mitigates legal culpability
Ensure Safety with Parking Security and Electronically Verified Guard Patrols
Employees, students, faculty, contractors and visitors are easily an organization’s most valuable assets, and maintaining a safe workplace is essential to creating a productive environment. While many companies have access control and/or video surveillance systems in place, when it comes to ensuring safety, an integrated RFID solution can help prevent incidents that can result in devastating loss and costly litigation.
The first step in ensuring safety is preventing incidents from occurring in the first place. RFID-based vehicle and driver identification solutions can secure parking areas and accurately identify vehicles in all weather conditions, and the technology is suitable for vehicle access barriers in city centers, airports, and government buildings.

‘Proof of visit’ or electronically verified guard patrols is another area where RFID adds tremendous life-safety value. Complicated, document-reliant guard patrols can involve high staffing costs and cumbersome reporting to ensure that legal guard tour requirements are met. It is nearly impossible to track every area that requires monitoring in an efficient and comprehensive manner; this can result in enormous administrative requirements and, in the worst case, incomplete reporting. Using RFID data collectors linked to maintenance-free and unobtrusive monitoring stations give patrolling guards an easy way to electronically record their rounds, providing reliable documentation and enhancing security.
Benefits
- Ensures life safety
- Reduces corporate liability

Conclusion
As customers continue to look for better ways to protect the things that matter most to their business, the merits of implementing RFID are clear. With myriad solutions available, customers will certainly be seeking the counsel of trusted integrators to help them navigate the strengths and weaknesses of various systems.
Start by asking these key questions:
Q. Is it intuitive?
The most important part of an RFID system is the software, which ties all the information associated with an item to the RFID tag and provides the details on the collection of evidence, chain-of-custody transfers and item location and condition. Check that the software is easy to use with inclusive dashboards and rich reports that provide everything needed at a glance.
The hardware (tags, cabinets, storage lockers, fobs, etc.) must be intuitive as well with LEDs that clearly indicate to the user how to use their tag, return assets, check out evidence, etc. If it isn’t easy, users will look for any way to avoid using it, and that puts security at risk.

Q. Will it connect to other business systems?
If you can do it in the standalone RFID solution, you should also be able to get that functionality in an integrated solution through one single software management solution. For example, if integrated with a physical access control system, the operator should be able to assign RFID tag privileges right along with any other door access privileges, from one single interface.
It’s easy to quickly discover which RFID manufacturers take their role in integration seriously. They’ll offer a robust SDK or API to ensure customers can get integrated and secure automation through intelligent combined systems that are designed to work as one. A clunky integration will allow essential details to fall through the cracks and/or make the solution difficult to use.

Q. How reliable is it?
A quick view of an RFID partner’s spec sheet can shed light on their solution’s overall reliability.
First, the mechanics of the solution must be rock-solid:
- Fobs that are constructed as a single piece that aren’t vulnerable to moisture and are contactless to support a longer lifespan
- Cabinets, smart storage lockers and key boxes that utilize multiple processors to avoid freezing up and requiring system reboots
- Locks that can be programmed as fail-secure vs. fail-safe. For spaces that contain critical or sensitive material, fail secure is the preferred condition as these lockset types do not release in a power disruption. The key difference between the two conditions:
– For fail-secure locks, power initiates the unlocking of the door.
– For fail-safe locks, loss of power initiates the unlocking of the door.
Q. What is the cost?
Look for RFID solutions that offer low introductory costs and do not require annual fees (other than software support agreements). Ask about VAR partnerships that have zero minimum sales requirements, so you can cost-effectively add the RFID line to your portfolio. For integrations, look for pricing models that best accommodate the type of environment your customer has. For example, escalating pricing models (small, medium, or large) may be the best way to guarantee scalability and flexibility for growing customers.


